This post will cover the detailed step by step process to deploy Keycloak in a production environment using AWS EC2 Server. We will use Docker containers and Maria DB as the database. For securing the portal, we will use NGINX and certbot to generate Letsencrypt certificate.
The steps can be broken down as following:
- Create a domain/subdomain to be used for Keycloak
- Create the EC2 Server in AWS with the correct inbound rule set
- Install NGINX and Certbot and configure it for Keycloak domain
- Install Docker and configure it to run without “sudo”
- Create docker-compose.yml file
- Bring up the container and validate everything
1. Create a Domain or Subdomain to be used for Keycloak
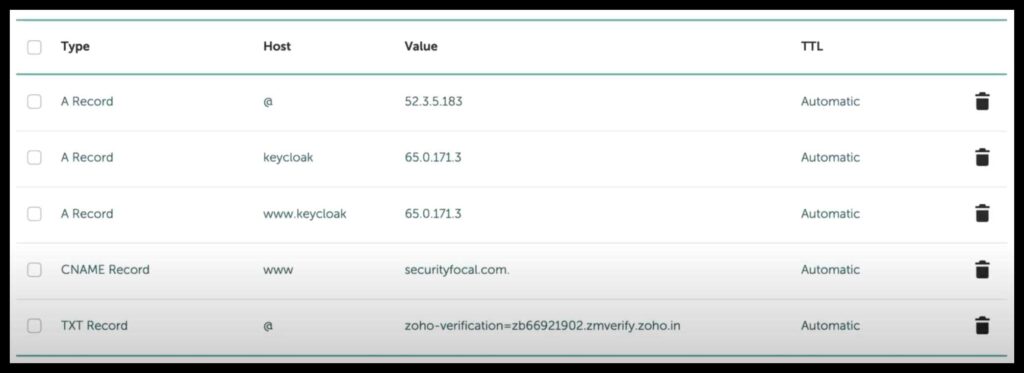
I have created an Elastic IP in AWS to be used for Keycloak. We are using a subdomain for an existing domain by creating an “A” record. Please refer to the following image for reference.
2. Create the EC2 Server in AWS Console
Login to your AWS account and create an Amazon EC2 Server. Please make sure to size it based on the expected load. The recommended minimum hardware is 2 core CPU & 4 GB RAM which we will use for this deployment.
Please make sure to allow inbound TCP ports 22, 80(required for certbot certificate creation), 443 and 8081 that we will be using in this deployment. Next map the Elastic ip address to the newly created Keycloak Server. Once the server is up, perform the package upgrade using following command
sudo apt update && sudo apt upgrade
Preparing to unpack …/42-snapd_2.66.1+22.04_amd64.deb …
Unpacking snapd (2.66.1+22.04) over (2.63+22.04ubuntu0.1) …
Preparing to unpack …/43-sosreport_4.7.2-0ubuntu1~22.04.2_amd64.deb …
Unpacking sosreport (4.7.2-0ubuntu1~22.04.2) over (4.5.6-0ubuntu1~22.04.2) …
Preparing to unpack …/44-amd64-microcode_3.20191218.1ubuntu2.3_amd64.deb …
Unpacking amd64-microcode (3.20191218.1ubuntu2.3) over (3.20191218.1ubuntu2.2) …
Preparing to unpack …/45-cloud-init_24.4-0ubuntu1~22.04.1_all.deb …
Unpacking cloud-init (24.4-0ubuntu1~22.04.1) over (24.3.1-0ubuntu0~22.04.1) …
Preparing to unpack …/46-intel-microcode_3.20241112.0ubuntu0.22.04.1_amd64.deb …
Unpacking intel-microcode (3.20241112.0ubuntu0.22.04.1) over (3.20240910.0ubuntu0.22.04.1) …
Setting up libexpat1:amd64 (2.4.7-1ubuntu0.5) …
Setting up snapd (2.66.1+22.04) …
Installing new version of config file /etc/apparmor.d/usr.lib.snapd.snap-confine.real …
Progress: [ 51%] [#############################………………………..]
Go ahead and reboot the server if required.
3. Install NGINX and configure it for Keycloak domain
Now we will install the NGINX
sudo apt install nginx
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
The following additional packages will be installed:
fontconfig-config fonts-dejavu-core libdeflate0 libfontconfig1 libgd3
libjbig0 libjpeg-turbo8 libjpeg8 libnginx-mod-http-geoip2
libnginx-mod-http-image-filter libnginx-mod-http-xslt-filter
libnginx-mod-mail libnginx-mod-stream libnginx-mod-stream-geoip2 libtiff5
libwebp7 libxpm4 nginx-common nginx-core
Suggested packages:
libgd-tools fcgiwrap nginx-doc ssl-cert
The following NEW packages will be installed:
fontconfig-config fonts-dejavu-core libdeflate0 libfontconfig1 libgd3
libjbig0 libjpeg-turbo8 libjpeg8 libnginx-mod-http-geoip2
libnginx-mod-http-image-filter libnginx-mod-http-xslt-filter
libnginx-mod-mail libnginx-mod-stream libnginx-mod-stream-geoip2 libtiff5
libwebp7 libxpm4 nginx nginx-common nginx-core
0 upgraded, 20 newly installed, 0 to remove and 0 not upgraded.
Need to get 2693 kB of archives.
After this operation, 8346 kB of additional disk space will be used.
Do you want to continue? [Y/n]
Type Y when prompted. Once the installation is completed, validate the NGINX Version using following command
nginx -v
nginx version: nginx/1.18.0 (Ubuntu)
sudo systemctl status nginx
● nginx.service – A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; vendor preset:>
Active: active (running) since Fri 2025-01-03 10:27:21 UTC; 1min 29s ago
Docs: man:nginx(8)
Process: 370 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_proces>
Process: 435 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (co>
Main PID: 443 (nginx)
Tasks: 2 (limit: 2338)
Memory: 11.6M
CPU: 35ms
CGroup: /system.slice/nginx.service
├─443 “nginx: master process /usr/sbin/nginx -g daemon on; master_>
└─445 “nginx: worker process” “” “” “” “” “” “” “” “” “” “” “” “” >
Jan 03 10:27:21 ip-172-31-41-6 systemd[1]: Starting A high performance web serv>
Jan 03 10:27:21 ip-172-31-41-6 systemd[1]: Started A high performance web serve>
lines 1-16/16 (END)…skipping…
● nginx.service – A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2025-01-03 10:27:21 UTC; 1min 29s ago
Docs: man:nginx(8)
Process: 370 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Process: 435 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Main PID: 443 (nginx)
Tasks: 2 (limit: 2338)
Memory: 11.6M
CPU: 35ms
CGroup: /system.slice/nginx.service
├─443 “nginx: master process /usr/sbin/nginx -g daemon on; master_process on;”
└─445 “nginx: worker process” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “” “”
Jan 03 10:27:21 ip-172-31-41-6 systemd[1]: Starting A high performance web server and a reverse proxy server…
Jan 03 10:27:21 ip-172-31-41-6 systemd[1]: Started A high performance web server and a reverse proxy server.
The output confirms that our NGINX is up and running
Next we will enable and configure the UFW to allow NGINX and ssh for remote connectivity.
sudo ufw status
Status: inactive
sudo ufw allow “Nginx Full”
Rules updated
Rules updated (v6)
sudo ufw allow ssh
Rules updated
Rules updated (v6)
sudo ufw enable
Command may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall is active and enabled on system startup
sudo ufw reload
Firewall reloaded
sudo ufw status
Status: active
To Action From
— —— —-
Nginx Full ALLOW Anywhere
22/tcp ALLOW Anywhere
Nginx Full (v6) ALLOW Anywhere (v6)
22/tcp (v6) ALLOW Anywhere (v6)
Next we will install certbot for Letsencrypt certificate creation and automated renewal
sudo apt install certbot python3-certbot-nginx
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
The following additional packages will be installed:
python3-acme python3-certbot python3-configargparse python3-icu python3-josepy
python3-parsedatetime python3-requests-toolbelt python3-rfc3339 python3-zope.component
python3-zope.event python3-zope.hookable
Suggested packages:
python-certbot-doc python3-certbot-apache python-acme-doc python-certbot-nginx-doc
The following NEW packages will be installed:
certbot python3-acme python3-certbot python3-certbot-nginx python3-configargparse python3-icu
python3-josepy python3-parsedatetime python3-requests-toolbelt python3-rfc3339
python3-zope.component python3-zope.event python3-zope.hookable
0 upgraded, 13 newly installed, 0 to remove and 0 not upgraded.
Need to get 993 kB of archives.
After this operation, 5077 kB of additional disk space will be used.
Do you want to continue? [Y/n] y
Click on Y to continue. Once the installation is successfully completed, next step will be to create out certificate. Run the following commands and provide all the required information.
sudo certbot –nginx -d keycloak.securityfocal.com -d www.keycloak.securityfocal.com
sudo certbot –nginx -d keycloak.securityfocal.com -d www.keycloak.securityfocal.com
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter ‘c’ to cancel): kumar@securityfocal.com
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.4-April-3-2024.pdf. You must agree in
order to register with the ACME server. Do you agree?
(Y)es/(N)o:y
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let’s Encrypt project and the non-profit organization that
develops Certbot? We’d like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
(Y)es/(N)o: y
Account registered.
Requesting a certificate for keycloak.securityfocal.com and www.keycloak.securityfocal.com
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/keycloak.securityfocal.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/keycloak.securityfocal.com/privkey.pem
This certificate expires on 2025-04-03.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
Deploying certificate
Successfully deployed certificate for keycloak.securityfocal.com to /etc/nginx/sites-enabled/default
Successfully deployed certificate for www.keycloak.securityfocal.com to /etc/nginx/sites-enabled/default
Congratulations! You have successfully enabled HTTPS on https://keycloak.securityfocal.com and https://www.keycloak.securityfocal.com
If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let’s Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Next we will do a dry run to validate if auto renewal is working as expected
sudo certbot renew –dry-run
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Processing /etc/letsencrypt/renewal/keycloak.securityfocal.com.conf
Account registered.
Simulating renewal of an existing certificate for keycloak.securityfocal.com and www.keycloak.securityfocal.com
Congratulations, all simulated renewals succeeded:
/etc/letsencrypt/live/keycloak.securityfocal.com/fullchain.pem (success)
Next we will configure NGINX for our deployment.
sudo unlink /etc/nginx/sites-enabled/default
cd /etc/nginx/sites-available/
sudo vi keycloak.securityfocal.conf
We will use following NGINX configuration for our Keycloak Deployment. Please make sure to change the configuration parameters as per your environment.
server {
listen 80;
server_name keycloak.securityfocal.com www.keycloak.securityfocal.com;
rewrite ^https://keycloak.securityfocal.com permanent;
}
server {
listen 443 ssl;
server_name keycloak.securityfocal.com www.keycloak.securityfocal.com;
ssl_certificate /etc/letsencrypt/live/keycloak.securityfocal.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/keycloak.securityfocal.com/privkey.pem;
ssl_session_cache builtin:1000 shared:ssl:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_pass http://65.0.171.3:8081;
}
}Save and close the file (:wq). Complete the NGINX configuration
sudo ln -s /etc/nginx/sites-available/keycloak.securityfocal.conf /etc/nginx/sites-enabled/keycloak.securityfocal.conf
sudo nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
sudo systemctl restart nginx
4. Install Docker and configure it to run without “sudo”
Create a keycloak directory in home directory
cd /home/ubuntu
sudo mkdir keycloak
cd keycloak
Next we will install Docker and Docker compose. To do that we will set up Docker’s apt repository.
sudo apt-get update
sudo apt-get install ca-certificates curl
Reading package lists… Done
Building dependency tree… Done
Reading state information… Done
ca-certificates is already the newest version (20240203~22.04.1).
ca-certificates set to manually installed.
curl is already the newest version (7.81.0-1ubuntu1.20).
curl set to manually installed.
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.asc
echo \
“deb [arch=$(dpkg –print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/ubuntu \
$(. /etc/os-release && echo “$VERSION_CODENAME”) stable” | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt-get update
Install Docker and Docker-Compose
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
sudo apt install docker-compose
Verify that the installation is successful by running the hello-world
sudo docker run hello-world
Unable to find image ‘hello-world:latest’ locally
latest: Pulling from library/hello-world
c1ec31eb5944: Pull complete
Digest: sha256:5b3cc85e16e3058003c13b7821318369dad01dac3dbb877aac3c28182255c724
Status: Downloaded newer image for hello-world:latest
Hello from Docker!
This message shows that your installation appears to be working correctly.
To generate this message, Docker took the following steps:
The Docker client contacted the Docker daemon.
The Docker daemon pulled the “hello-world” image from the Docker Hub.
(amd64)
The Docker daemon created a new container from that image which runs the
executable that produces the output you are currently reading.
The Docker daemon streamed that output to the Docker client, which sent it
to your terminal.
To try something more ambitious, you can run an Ubuntu container with:
$ docker run -it ubuntu bash
Share images, automate workflows, and more with a free Docker ID:
https://hub.docker.com/
For more examples and ideas, visit:
https://docs.docker.com/get-started/
This command downloads a test image and runs it in a container. When the container runs, it prints a confirmation message and exits.
To run Docker without root privileges, use the following commands
sudo groupadd docker
sudo usermod -aG docker $USER
Log out and log back in so that your group membership is re-evaluated.
5. Create docker-compose.yml file
We now need to create our docker-compose file. You may use the following code for that, please make sure to change the key parameters:
sudo vi docker-compose.yml
services:
mariadb:
image: mariadb:latest
environment:
MARIADB_ROOT_PASSWORD: toor
MARIADB_DATABASE: keycloak
MARIADB_USER: keycloak
MARIADB_PASSWORD: keycloak
mem_limit: 300m
container_name: mariadb
restart: always
volumes:
- mariadb_data:/var/lib/mysql
networks:
- keycloak-auth
keycloak:
image: quay.io/keycloak/keycloak:latest
environment:
KC_DB: mariadb
KC_DB_SCHEMA: keycloak
KC_DB_USERNAME: keycloak
KC_DB_PASSWORD: keycloak
KC_DB_URL_HOST: mariadb
KEYCLOAK_ADMIN: admin
KEYCLOAK_ADMIN_PASSWORD: admin
KC_PROXY_HEADERS: xforwarded
KC_HTTP_ENABLED: "true"
KC_HOSTNAME_STRICT: "false"
KC_HOSTNAME_URL: https://mydomain
mem_limit: 500m
ports:
- 8443:8443
- 8081:8080
container_name: keycloak
restart: always
networks:
- keycloak-auth
depends_on:
- mariadb
command: start
volumes:
mariadb_data:
driver: local
networks:
keycloak-auth:
driver: bridgeYou can use following github repository also for reference: docker-compose.yml. Please make sure to change the respective values as required for your deployment.6. Bring up the container and validate everything
docker-compose up
Using username “ubuntu”.
Authenticating with public key “imported-openssh-key”
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 6.8.0-1021-aws x86_64)
Documentation: https://help.ubuntu.com
Management: https://landscape.canonical.com
Support: https://ubuntu.com/pro
System information as of Fri Jan 3 11:08:37 UTC 2025
System load: 0.0 Processes: 106
Usage of /: 36.1% of 7.57GB Users logged in: 0
Memory usage: 14% IPv4 address for eth0: 172.31.41.6
Swap usage: 0%
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
New release ‘24.04.1 LTS’ available.
Run ‘do-release-upgrade’ to upgrade to it.
Last login: Fri Jan 3 11:00:43 2025 from 106.51.76.126
ubuntu@ip-172-31-41-6:~$ cd keycloak/
ubuntu@ip-172-31-41-6:~/keycloak$ docker-compose up
Creating network “keycloak_keycloak-auth” with driver “bridge”
Creating volume “keycloak_mariadb_data” with local driver
Pulling mariadb (mariadb:latest)…
latest: Pulling from library/mariadb
de44b265507a: Pull complete
ca9b21d0c985: Pull complete
041c753879ae: Pull complete
e7b5137dc4b2: Pull complete
655e5d2590bd: Pull complete
41b3170b5f12: Pull complete
95adc28016bc: Pull complete
407e9d6eefb4: Pull complete
Digest: sha256:a9547599cd87d7242435aea6fda22a9d83e2c06d16c658ef70d2868b3d3f6a80
Status: Downloaded newer image for mariadb:latest
Pulling keycloak (quay.io/keycloak/keycloak:latest)…
latest: Pulling from keycloak/keycloak
3db38ca7c9bc: Pull complete
83a2d69b614f: Pull complete
835348ea4429: Pull complete
fe4d0ad1ea3d: Pull complete
Digest: sha256:4388e2379b7e870a447adbe7b80bd61f5fbf04e925832b19669fda4957f05a81
Status: Downloaded newer image for quay.io/keycloak/keycloak:latest
Creating mariadb … done
Creating keycloak … done
Attaching to mariadb, keycloak
mariadb | 2025-01-03 11:09:15+00:00 [Note] [Entrypoint]: Entrypoint script f or MariaDB Server 1:11.6.2+maria~ubu2404 started.
mariadb | 2025-01-03 11:09:16+00:00 [Warn] [Entrypoint]: /sys/fs/cgroup///me mory.pressure not writable, functionality unavailable to MariaDB
mariadb | 2025-01-03 11:09:16+00:00 [Note] [Entrypoint]: Switching to dedica ted user ‘mysql’
mariadb | 2025-01-03 11:09:16+00:00 [Note] [Entrypoint]: Entrypoint script f or MariaDB Server 1:11.6.2+maria~ubu2404 started.
mariadb | 2025-01-03 11:09:16+00:00 [Note] [Entrypoint]: Initializing databa se files
mariadb | 2025-01-03 11:09:16 0 [Warning] mariadbd: io_uring_queue_init() fa iled with errno 95
mariadb | 2025-01-03 11:09:16 0 [Warning] InnoDB: liburing disabled: falling back to innodb_use_native_aio=OFF
keycloak | Changes detected in configuration. Updating the server image.
mariadb | 2025-01-03 11:09:18+00:00 [Note] [Entrypoint]: Database files init ialized
mariadb | 2025-01-03 11:09:18+00:00 [Note] [Entrypoint]: Starting temporary server
mariadb | 2025-01-03 11:09:18+00:00 [Note] [Entrypoint]: Waiting for server startup
mariadb | 2025-01-03 11:09:18 0 [Note] Starting MariaDB 11.6.2-MariaDB-ubu24 04 source revision d8dad8c3b54cd09fefce7bc3b9749f427eed9709 server_uid 72+4ASMvY xproTQgRqIDplDA1XA= as process 85
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Compressed tables use zlib 1. 3
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Number of transaction pools: 1
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Using crc32 + pclmulqdq instr uctions
mariadb | 2025-01-03 11:09:18 0 [Note] mariadbd: O_TMPFILE is not supported on /tmp (disabling future attempts)
mariadb | 2025-01-03 11:09:18 0 [Warning] mariadbd: io_uring_queue_init() fa iled with errno 95
mariadb | 2025-01-03 11:09:18 0 [Warning] InnoDB: liburing disabled: falling back to innodb_use_native_aio=OFF
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Initializing buffer pool, tot al size = 128.000MiB, chunk size = 2.000MiB
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Completed initialization of b uffer pool
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: File system buffers for log d isabled (block size=512 bytes)
keycloak | Updating the configuration and installing your custom providers, i f any. Please wait.
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: End of log at LSN=47763
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Opened 3 undo tablespaces
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: 128 rollback segments in 3 un do tablespaces are active.
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: Setting file ‘./ibtmp1’ size to 12.000MiB. Physically writing the file full; Please wait …
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: File ‘./ibtmp1’ size is now 1 2.000MiB.
mariadb | 2025-01-03 11:09:18 0 [Note] InnoDB: log sequence number 47763; tr ansaction id 14
mariadb | 2025-01-03 11:09:18 0 [Note] Plugin ‘FEEDBACK’ is disabled.
mariadb | 2025-01-03 11:09:18 0 [Note] Plugin ‘wsrep-provider’ is disabled.
mariadb | 2025-01-03 11:09:29 0 [Note] mariadbd: Event Scheduler: Loaded 0 e vents
mariadb | 2025-01-03 11:09:30 0 [Note] mariadbd: ready for connections.
mariadb | Version: ‘11.6.2-MariaDB-ubu2404’ socket: ‘/run/mysqld/mysqld.soc k’ port: 0 mariadb.org binary distribution
mariadb | 2025-01-03 11:09:30+00:00 [Note] [Entrypoint]: Temporary server st arted.
mariadb | 2025-01-03 11:09:31+00:00 [Note] [Entrypoint]: Creating database k eycloak
mariadb | 2025-01-03 11:09:31+00:00 [Note] [Entrypoint]: Creating user keycl oak
mariadb | 2025-01-03 11:09:31+00:00 [Note] [Entrypoint]: Giving user keycloa k access to schema keycloak
mariadb | 2025-01-03 11:09:31+00:00 [Note] [Entrypoint]: Securing system use rs (equivalent to running mysql_secure_installation)
mariadb |
mariadb | 2025-01-03 11:09:32+00:00 [Note] [Entrypoint]: Stopping temporary server
mariadb | 2025-01-03 11:09:32 0 [Note] mariadbd (initiated by: unknown): Nor mal shutdown
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: FTS optimize thread exiting.
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Starting shutdown…
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Dumping buffer pool(s) to /va r/lib/mysql/ib_buffer_pool
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Buffer pool(s) dump completed at 250103 11:09:32
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Removed temporary tablespace data file: “./ibtmp1”
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Shutdown completed; log seque nce number 47763; transaction id 15
mariadb | 2025-01-03 11:09:32 0 [Note] mariadbd: Shutdown complete
mariadb |
mariadb | 2025-01-03 11:09:32+00:00 [Note] [Entrypoint]: Temporary server st opped
mariadb |
mariadb | 2025-01-03 11:09:32+00:00 [Note] [Entrypoint]: MariaDB init proces s done. Ready for start up.
mariadb |
mariadb | 2025-01-03 11:09:32 0 [Note] Starting MariaDB 11.6.2-MariaDB-ubu24 04 source revision d8dad8c3b54cd09fefce7bc3b9749f427eed9709 server_uid 72+4ASMvY xproTQgRqIDplDA1XA= as process 1
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Compressed tables use zlib 1. 3
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Number of transaction pools: 1
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Using crc32 + pclmulqdq instr uctions
mariadb | 2025-01-03 11:09:32 0 [Note] mariadbd: O_TMPFILE is not supported on /tmp (disabling future attempts)
mariadb | 2025-01-03 11:09:32 0 [Warning] mariadbd: io_uring_queue_init() fa iled with errno 95
mariadb | 2025-01-03 11:09:32 0 [Warning] InnoDB: liburing disabled: falling back to innodb_use_native_aio=OFF
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Initializing buffer pool, tot al size = 128.000MiB, chunk size = 2.000MiB
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Completed initialization of b uffer pool
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: File system buffers for log d isabled (block size=512 bytes)
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: End of log at LSN=47763
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Opened 3 undo tablespaces
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: 128 rollback segments in 3 un do tablespaces are active.
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Setting file ‘./ibtmp1’ size to 12.000MiB. Physically writing the file full; Please wait …
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: File ‘./ibtmp1’ size is now 1 2.000MiB.
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: log sequence number 47763; tr ansaction id 14
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Loading buffer pool(s) from / var/lib/mysql/ib_buffer_pool
mariadb | 2025-01-03 11:09:32 0 [Note] Plugin ‘FEEDBACK’ is disabled.
mariadb | 2025-01-03 11:09:32 0 [Note] Plugin ‘wsrep-provider’ is disabled.
mariadb | 2025-01-03 11:09:32 0 [Note] InnoDB: Buffer pool(s) load completed at 250103 11:09:32
mariadb | 2025-01-03 11:09:36 0 [Note] Server socket created on IP: ‘0.0.0.0 ‘.
mariadb | 2025-01-03 11:09:36 0 [Note] Server socket created on IP: ‘::’.
mariadb | 2025-01-03 11:09:36 0 [Note] mariadbd: Event Scheduler: Loaded 0 e vents
mariadb | 2025-01-03 11:09:36 0 [Note] mariadbd: ready for connections.
mariadb | Version: ‘11.6.2-MariaDB-ubu2404’ socket: ‘/run/mysqld/mysqld.soc k’ port: 3306 mariadb.org binary distribution
keycloak | 2025-01-03 11:09:47,958 INFO io.qua.dep.QuarkusAugmentor Quarkus augmentation completed in 25188ms
keycloak | Server configuration updated and persisted. Run the following comm and to review the configuration:
keycloak |
keycloak | kc.sh show-config
keycloak |
keycloak | Next time you run the server, just run:
keycloak |
keycloak | kc.sh start –optimized
keycloak |
keycloak | 2025-01-03 11:09:50,142 ERROR org.keycloak.quarkus.runtime.config uration.mappers.PropertyMappers Hostname v1 options [hostname-url] are s till in use, please review your configuration
keycloak | 2025-01-03 11:09:56,440 INFO org.keycloak.quarkus.runtime.storag e.infinispan.CacheManagerFactory Starting Infinispan embedded cache mana ger
keycloak | 2025-01-03 11:09:57,969 INFO [org.infinispan.CONTAINER] (Thread-5 ) ISPN000556: Starting user marshaller ‘org.infinispan.commons.marshall.Immutabl eProtoStreamMarshaller’
keycloak | 2025-01-03 11:09:58,753 WARN [org.jgroups.stack.Configurator] (Th read-5) JGRP000014: ThreadPool.thread_dumps_threshold has been deprecated: ignor ed
keycloak | 2025-01-03 11:09:58,788 INFO org.infinispan.CLUSTER ISPN000078: Starting JGroups channel ISPN with stack udp
keycloak | 2025-01-03 11:09:58,791 INFO org.jgroups.JChannel lo cal_addr: 60bda999-48d7-484d-bf33-83d185ac3eae, name: 2bafd081979e-49370
keycloak | 2025-01-03 11:09:58,820 WARN [org.jgroups.protocols.UDP] (Thread- 5) JGRP000015: the send buffer of socket MulticastSocket was set to 1MB, but the OS only allocated 212.99KB
keycloak | 2025-01-03 11:09:58,821 WARN [org.jgroups.protocols.UDP] (Thread- 5) JGRP000015: the receive buffer of socket MulticastSocket was set to 20MB, but the OS only allocated 212.99KB
keycloak | 2025-01-03 11:09:58,822 WARN [org.jgroups.protocols.UDP] (Thread- 5) JGRP000015: the send buffer of socket MulticastSocket was set to 1MB, but the OS only allocated 212.99KB
keycloak | 2025-01-03 11:09:58,824 WARN [org.jgroups.protocols.UDP] (Thread- 5) JGRP000015: the receive buffer of socket MulticastSocket was set to 25MB, but the OS only allocated 212.99KB
keycloak | 2025-01-03 11:09:58,844 INFO [org.jgroups.protocols.FD_SOCK2] (Th read-5) server listening on *.25581
keycloak | 2025-01-03 11:09:59,482 WARN org.mariadb.jdbc.message.server.Err orPacket Error: 1146-42S02: Table ‘keycloak.MIGRATION_MODEL’ doesn’t exi st
keycloak | 2025-01-03 11:10:00,867 INFO [org.jgroups.protocols.pbcast.GMS] ( Thread-5) 2bafd081979e-49370: no members discovered after 2008 ms: creating clus ter as coordinator
keycloak | 2025-01-03 11:10:00,892 INFO org.infinispan.CLUSTER ISPN000094: Received new cluster view for channel ISPN: [2bafd081979e-49370|0] ( 1) [2bafd081979e-49370]
keycloak | 2025-01-03 11:10:01,126 INFO org.infinispan.CLUSTER ISPN000079: Channel ISPN local address is 2bafd081979e-49370, physical addre sses are [172.18.0.3:41117]
keycloak | 2025-01-03 11:10:01,187 WARN org.mariadb.jdbc.message.server.Err orPacket Error: 1146-42S02: Table ‘keycloak.DATABASECHANGELOG’ doesn’t e xist
keycloak | 2025-01-03 11:10:01,842 WARN liquibase.changelog.DatabaseChangeL og Due to mariadb SQL limitations, modifyDataType will lose primary key/ autoincrement/not null/comment settings explicitly redefined in the change. Use or to re-specify all configuration if this is the case
keycloak | 2025-01-03 11:10:01,844 WARN liquibase.changelog.DatabaseChangeL og Due to mariadb SQL limitations, setNullable will lose primary key/aut oincrement/not null/comment settings explicitly redefined in the change. Use or to re-specify all configuration if this is the case
keycloak | 2025-01-03 11:10:01,908 WARN org.mariadb.jdbc.message.server.Err orPacket Error: 1146-42S02: Table ‘keycloak.DATABASECHANGELOGLOCK’ doesn ‘t exist
keycloak | 2025-01-03 11:10:02,056 WARN org.mariadb.jdbc.message.server.Err orPacket Error: 1146-42S02: Table ‘keycloak.DATABASECHANGELOG’ doesn’t e xist
keycloak | 2025-01-03 11:10:02,058 INFO org.keycloak.quarkus.runtime.storag e.database.liquibase.QuarkusJpaUpdaterProvider Initializing database sch ema. Using changelog META-INF/jpa-changelog-master.xml
keycloak | 2025-01-03 11:10:03,118 WARN liquibase.changelog.DatabaseChangeL og Due to mariadb SQL limitations, modifyDataType will lose primary key/ autoincrement/not null/comment settings explicitly redefined in the change. Use or to re-specify all configuration if this is the case
keycloak | 2025-01-03 11:10:03,121 WARN liquibase.changelog.DatabaseChangeL og Due to mariadb SQL limitations, setNullable will lose primary key/aut oincrement/not null/comment settings explicitly redefined in the change. Use or to re-specify all configuration if this is the case
keycloak | 2025-01-03 11:10:03,359 WARN liquibase.changelog.DatabaseChangeL og Due to mariadb SQL limitations, modifyDataType will lose primary key/ autoincrement/not null/comment settings explicitly redefined in the change. Use or to re-specify all configuration if this is the case
keycloak | 2025-01-03 11:10:03,361 WARN liquibase.changelog.DatabaseChangeL og Due to mariadb SQL limitations, setNullable will lose primary key/aut oincrement/not null/comment settings explicitly redefined in the change. Use or to re-specify all configuration if this is the case
keycloak |
keycloak | UPDATE SUMMARY
keycloak | Run: 148
keycloak | Previously run: 0
keycloak | Filtered out: 0
keycloak | ——————————-
keycloak | Total change sets: 148
keycloak |
keycloak | 2025-01-03 11:10:24,433 WARN io.agroal.pool Datasource ”: JDBC resources leaked: 2 ResultSet(s) and 0 Statement(s)
keycloak | 2025-01-03 11:10:25,076 INFO org.keycloak.connections.infinispan.DefaultInfinispanConnectionProviderFactory Node name: 2bafd081979e-49370, Site name: null
keycloak | 2025-01-03 11:10:25,455 INFO org.keycloak.broker.provider.AbstractIdentityProviderMapper Registering class org.keycloak.broker.provider.mappersync.ConfigSyncEventListener
keycloak | 2025-01-03 11:10:25,488 INFO org.keycloak.services KC-SERVICES0050: Initializing master realm
keycloak | 2025-01-03 11:10:30,172 WARN org.keycloak.services KC-SERVICES0110: Environment variable ‘KEYCLOAK_ADMIN’ is deprecated, use ‘KC_BOOTSTRAP_ADMIN_USERNAME’ instead
keycloak | 2025-01-03 11:10:30,175 WARN org.keycloak.services KC-SERVICES0110: Environment variable ‘KEYCLOAK_ADMIN_PASSWORD’ is deprecated, use ‘KC_BOOTSTRAP_ADMIN_PASSWORD’ instead
keycloak | 2025-01-03 11:10:30,658 INFO org.keycloak.services KC-SERVICES0077: Created temporary admin user with username admin
keycloak | 2025-01-03 11:10:30,721 WARN io.agroal.pool Datasource ”: JDBC resources leaked: 1 ResultSet(s) and 0 Statement(s)
keycloak | 2025-01-03 11:10:31,002 INFO io.quarkus Keycloak 26.0.7 on JVM (powered by Quarkus 3.15.1) started in 42.773s. Listening on: http://0.0.0.0:8080
keycloak | 2025-01-03 11:10:31,004 INFO io.quarkus Profile prod activated.
keycloak | 2025-01-03 11:10:31,004 INFO io.quarkus Installed features: [agroal, cdi, hibernate-orm, jdbc-mariadb, keycloak, narayana-jta, opentelemetry, reactive-routes, rest, rest-jackson, smallrye-context-propagation, vertx]
If you have followed all the steps correctly, the Keycloak Server should come up
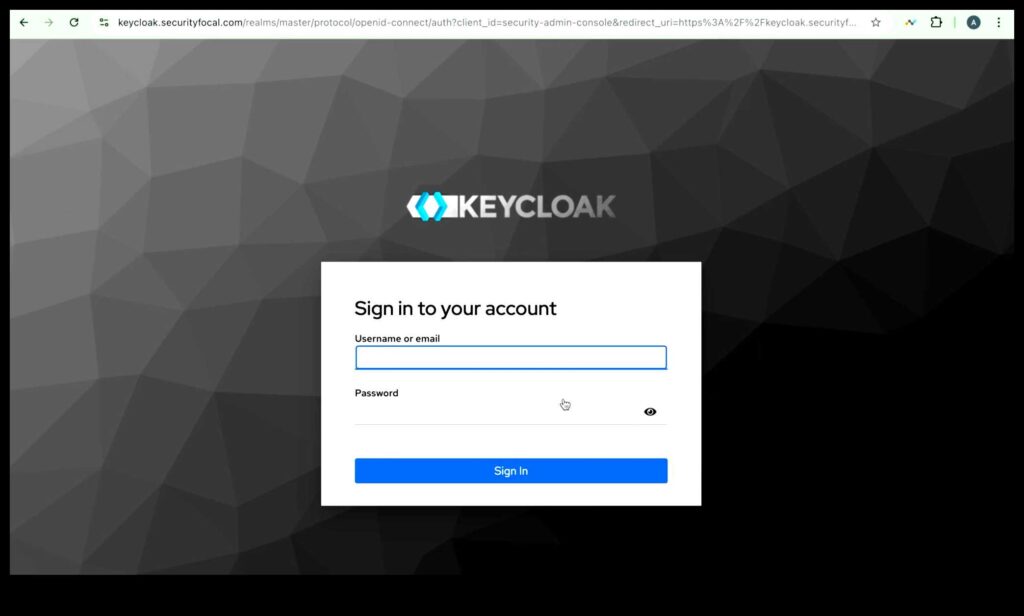
That’s it our server is ready. Use the admin credentials to login.